How To Be "Notified" When Config Files Have Been Changed Centos
Apparently changes of config files are critical and sensitive. For example, change of authorized_keys file probably indicates more than people can ssh to your servers now. When *.yml or *.conf has been changed, the beliefs of your application may change a lot, which may even result in data loss. And this happens typically when dev team are helping to practise problem shooting or hotfix the prod env.
As Ops/DevOps, I know you want to have all these changes to be certified and authorized through automation scripts. What'southward amend, the change is verified in integration exam. Yes, that volition put things nether good control and nosotros're more confident about the system's beliefs. But let's face it, business concern requires the states to be lean and adpative to changes. So y'all volition have surprise. It'southward amend we call back about the side by side topic: How Do Nosotros Detect And Audit All These Changes?
As stop users, here is my requirements:
- Monitor a list of conf files in critical envs. Be notified, when they have been inverse automatically.
- The bear on to my envs should exist as minimal as possible. The setup and configuration should be unproblematic and fast. The resources overhead should be small.
To achieve this, we may have different methods. i. We can subscribe to linux file modification events by inotify. 2. Identify config files into a local git repo. 3. Peridocially do the files/folder comparing and copy. Hither we cull method one, since it'south easier and more powerful.
We can use inotify to monitor a list of files/folders. Once they are changed, nosotros can get notified.
# Install packet
sudo apt-go install -y inotify-tools
# CentOS: yum install inotify-tools # Monitor a list of files
/usr/bin/inotifywait -d -one thousand -e modify \
--timefmt '%Y-%grand-%d %H:%M:%S' --format '%T %w %eastward %f' \
-r /etc/apt/sources.list.d /root/.ssh/authorized_keys /etc/hosts \
--outfile /root/monitor_server_filechanges.log # Confirm process
ps -ef | grep inotify # Run basic exam
echo "# exam" >> /root/.ssh/authorized_keys
tail /root/monitor_server_filechanges.log
# Sample output:
# root@denny-laptop:~# tail /root/monitor_server_filechanges.log
# 2016-06-25 11:31:34 /root/.ssh/authorized_keys Alter
# 2016-06-25 11:31:39 /root/.ssh/authorized_keys Modify
From above instance, nosotros can easily record critical info of the change: Inverse file listing and Timestamp. If we have backup of previous version, nosotros can run diff command to become the detail change of each file. Information technology'southward a pity that linux doesn't export pid of the change, so inotify can't tell u.s.a. which procedure has changed our interested files. That'south fine for usa in most cases.
To enable people easily to use it, I wrap upwards everything every bit a Jenkins chore. Thus yous only demand to do basic setting and one button click. Now you're on top of those critical changes!
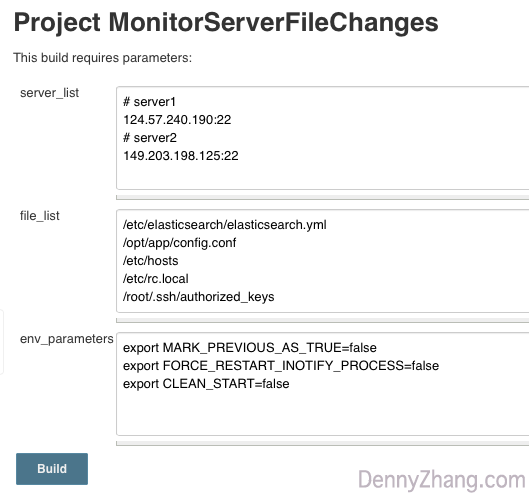
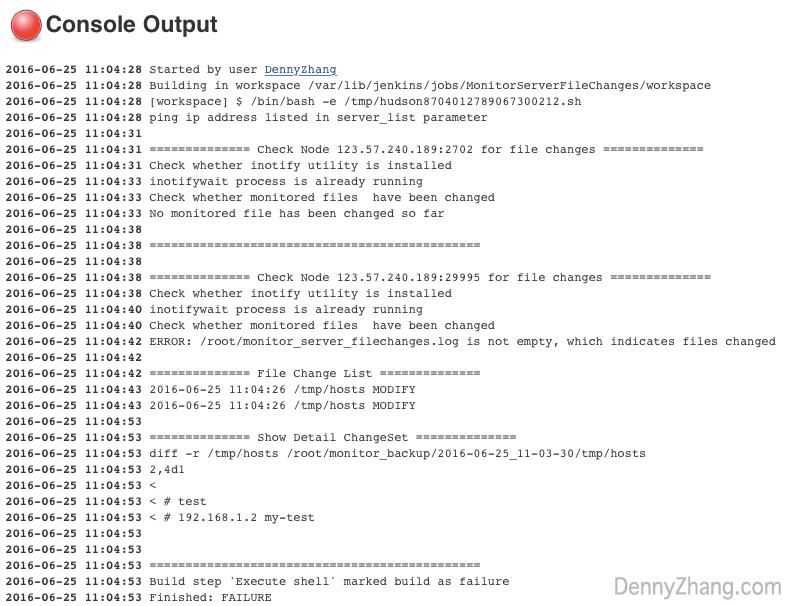
Detail implementation can be found in Github: Courage of Jenkins job and Jenkins job setting
Source: https://medium.com/@dennyzhang001/oops-my-config-files-have-been-changed-40ef3e1a8665
Posted by: bohntheirried.blogspot.com

0 Response to "How To Be "Notified" When Config Files Have Been Changed Centos"
Post a Comment